|
|
| Zeile 1: |
Zeile 1: |
| − | <br>The base is the point where the key is utilized to rotate the cam. You will see that the contact points can easily be spotted for a continuity test. The second is it is usually feasible to acquire, from various lock manufacturers, cylinders in various formats that can all be utilized with the same kind of key. To start with, door locks is a mechanical or electrical device that is utilised to enclosed property like the door of your home, or vehicle. Skeleton keys are available even today in houses which were built before 1940s. <br><br><br>Advances in lock technology appear to be met with new methods of breaking front door locks. After that you're making money. The majority of the time the GPU card will quit working because of a terrible risers after a number of hours or a day. Just ensure there aren't any graphics cards plugged in in case you use the onboard video. As an option, you can purchase AMD RX480 graphics cards rather than Fury's. <br><br><br>The lock is not any different by design or function. There are many sorts of door locks and the above mentioned are the most frequent. Unusual features These locks incorporate several unusual characteristics that donate to their security and dependability. Many bump-resistant locks are available which may not be easily opened via the lock bumping method. <br><br><br>A key is principally utilized to open a lock. If you enjoyed this article and you would certainly such as to obtain more details concerning [http://www.kg-machinery.com/ large cam lock] kindly browse through our web page. It is only a lock with extra security pins. There are various types of locks that we're using today. It's also referred to as Disc Tumbler Lock. <br> <br>The idea is to receive a simple computer built, troubleshoot any prospective problems, install the operating system and application, then construct the remainder of the machine. Remember is it is all relative. A number of them do the job at extremely competitive rates. With all these locks on the market these days, not all them offer genuine high-security. Therefore, there's no demand for 50 lock picks. Long gone are the times when a hairpin or a bent coat-hanger could select any lock. Normally, if there's a removable back on the dryer, then that is the location where you will locate the fuse. <br><br><br>Changing a couple of top springs to a firmer spring changes the ricochet tuning of the best pins, which makes it tough to bump. This set also provides a terrific collection of picks including a Peterson Reach, a tool very similar to the Hooked Diamond that's not only ideal for picking behind low set pins but also ideal for rotating pins if you become into picking high security locks. So your very first set ought to be in that range. A lock pick set needs to be designed around the sort of lock that you want to compromise. <br> Disc Tumbler Cam Lock <br>1 clip is given with each coupling. The most useful quality of these locks, nevertheless, is that their keys are restricted and can't be easily copied. The fundamental design has been utilized for at least 50 decades, with the sophisticated security features in the most recent models dating back almost 40 decades. Many different models are produced over the previous 50 decades, in a number of finishes and with various security features. You're still just paying for the case and extra fluff tools which you will never need or use. So you are spending now paying $32 for the circumstance! It is possible to purchase a SouthOrd leather case but they're pretty crappy. <br><br><br>For the time being, just place a connector on the end nearest the receiveryou'll want to find the opposite end outside before it's possible to place the plug on. Medeco did release a special kind of pin named ARX pins that should help it become harder to bypass their locks utilizing certain specialized tools, but these pins can be hard to obtain from Medeco if you would like to upgrade existing Medeco locks. The total spinner is really thick to permit for the detail of the head, so designer developed a bearing cap that is a lot thicker. Ball-lock, Figure 1, is the most frequent design and has the widest selection of applications. <br><br><br>You ought to be constantly varying tension. Modifying the spring tension can decrease bumping. The pressure is going to keep the pin rotations in place, and permit the lock to be attacked. Hydraulic fluids and many different liquids and a few gases require two way shut-off. Also take note that couplings could possibly be subjected to pressures well over the maximum operating pressure. Consequently, check with the manufacturer to learn whether the coupling will tolerate these ailments. The Twistlok coupling is twist to release and is quite a long established, superior quality durable product employed in factories throughout the world. <br><br><br>Industrial hose fittings made available by PT are created from a number of materials, with selection based on application. Tighten this in the exact manor only this time you'll be turning the hose instead. You likely apply your air compressor hose for a diverse chain of tasks. The plug functions as a partial curtain, holding the key in position with regard to the lever throw. <br>
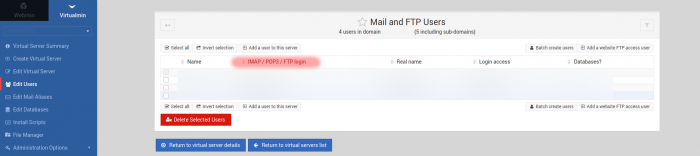
| + | 1. Bitte entnehmen Sie die Zugangsdaten (Benutzername + Passwort) der User Liste im Webserver Webinterface: |
| | + | |
| | + | [[Datei:Screenshot_email_users_virtualmin.png|700px]] |
| | + | |
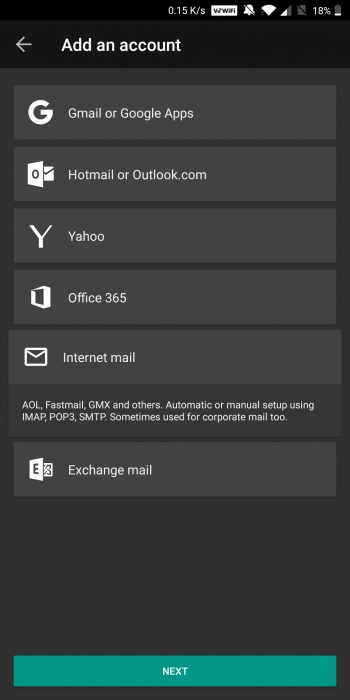
| | + | 2. Bitte wählen Sie `Internet mail` |
| | + | |
| | + | [[Datei:Aquamail_0.jpg|350px]] |
| | + | |
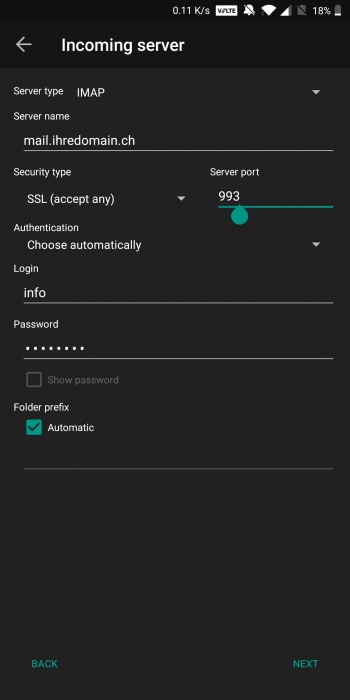
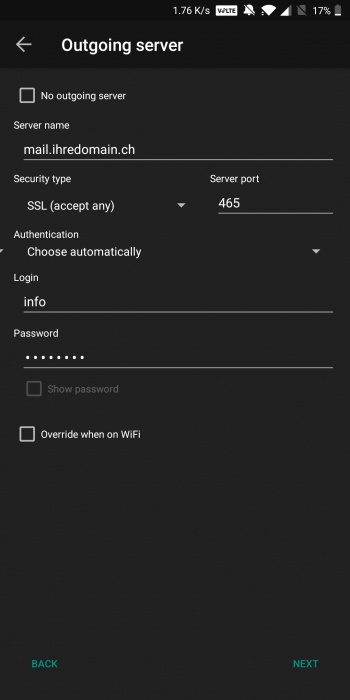
| | + | 3. Der Server name setzt sich üblicherweise aus mail.ihredomain.ch zusammen. Sollte dies nicht funktionieren bitten wir Sie uns zu kontaktieren. Füllen Sie die Formulare für `Incoming` und `Outgoing Server` wie folgend beschrieben aus. Verwenden Sie für `Login` den Benutzer von der am Anfang beschriebenen User Liste vom Webserver Webinterface. Achten Sie jeweils auf die `Security type` und `Port` Einstellungen. |
| | + | |
| | + | [[Datei:Aquamail_1.jpg|350px]] |
| | + | |
| | + | [[Datei:Aquamail_2.jpg|350px]] |
| | + | |
| | + | |
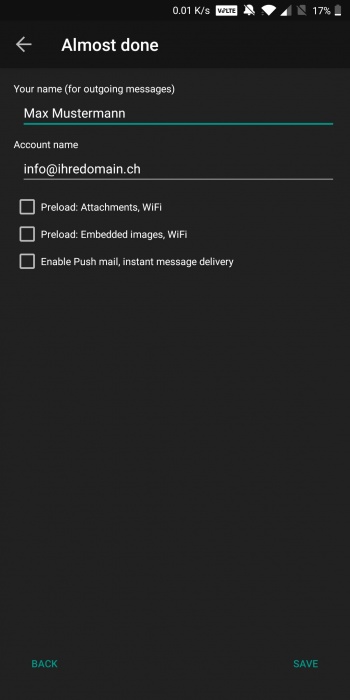
| | + | 4. `Your Name` und `Account name` können wie gewünscht ausgefüllt werden. |
| | + | |
| | + | [[Datei:Aquamail_3.jpg|350px]] |
Aktuelle Version vom 19. Februar 2020, 21:00 Uhr
1. Bitte entnehmen Sie die Zugangsdaten (Benutzername + Passwort) der User Liste im Webserver Webinterface:
2. Bitte wählen Sie `Internet mail`
3. Der Server name setzt sich üblicherweise aus mail.ihredomain.ch zusammen. Sollte dies nicht funktionieren bitten wir Sie uns zu kontaktieren. Füllen Sie die Formulare für `Incoming` und `Outgoing Server` wie folgend beschrieben aus. Verwenden Sie für `Login` den Benutzer von der am Anfang beschriebenen User Liste vom Webserver Webinterface. Achten Sie jeweils auf die `Security type` und `Port` Einstellungen.
4. `Your Name` und `Account name` können wie gewünscht ausgefüllt werden.